NetAnswer takes care of the security of your data every day. In particular, we have implemented irreversible password encryption that makes it impossible for even NetAnswer to access them. However, some of our customers, and probably some of their members, receive ransomware emails where their passwords are written in clear text. Here is the cause.
For more than a year, a large e-mail scam campaign has been going on. It consists of blackmail in exchange for a payment via Bitcoin to ensure the hacker’s silence.
Here’s what the email may look like:
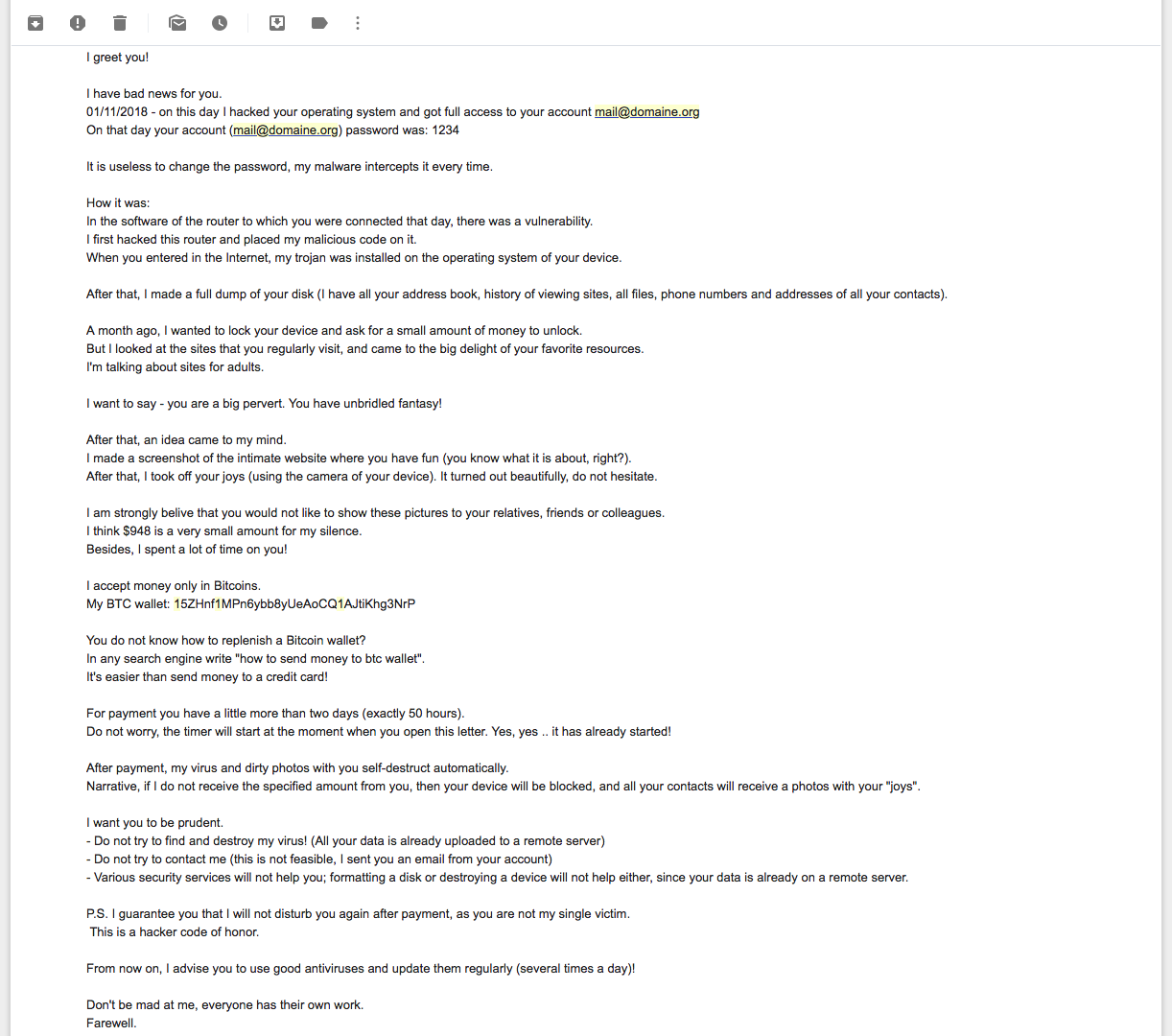
The hacker claims that there was a security breach in your router, that a virus (trojan) infected your computer in order to retrieve your password and contacts, that screenshots of sites not divulgeable to your entourage were taken or that your webcam was monitored and images of you recorded during intimate moments.
There are 3 reasons why this scam has been so successful:
- the sender of the e-mail usually uses the victim’s address or a business address close to the victim, as its technicality allows it to pass the spam filters,
- the allegations made against the victim are likely to be heard, as pornographic sites are among the most visited in the world
- the sender of this e-mail claims to have hacked the recipient’s account, providing his password as proof.
If this last point has convinced many victims, rest assured, there is little chance that your computer has been infected and checked. Indeed, the fact that the hacker can display your password “simply” and unfortunately reveals a leak of your data on another site. Indeed in 2012, Linkedin, DropBox, Facebook have all been hacked, so there are historical databases of old passwords that surely look like recently used passwords… because very often passwords are not changed, or if they are, they vary very little (adding or changing one or more characters, changing the date…).
First thing to do, fill in your e-mail addresses using the same password on this site: https://haveibeenpwned.com/ which lists all the addresses that have been leaked on sites of varying sizes, such as LinkedIn for example. If you use the same password as the leaked addresses, it is not surprising to see it displayed in the email you received.
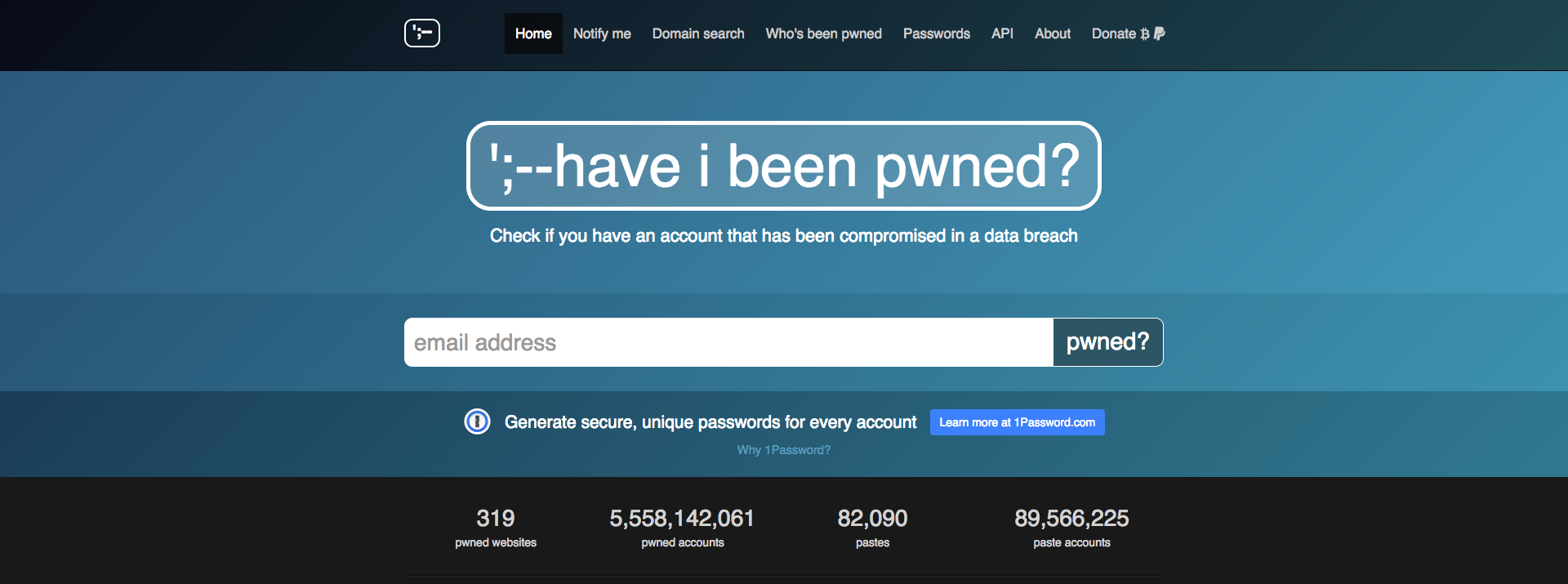
Then, make sure that all the accounts where you use the same password have not been altered and change your password immediately (we will carefully avoid birth dates or other “1234”). We can only advise you to have different passwords per site.
To manage your passwords, you can look at LastPass, Dashlane or 1Password.
Finally, even if your computer has not been infected, you can scan your computer (for free) with Malwarebytes available for download here. Even if these emails are not risky in themselves, they remind us of the need not to take the management of our data lightly. To learn more, we invite you to take the ANSSI MOOC for free (until April 2019): https://secnumacademie.gouv.fr/ which will train you in the basics of cybersecurity or allow you to deepen your knowledge.

In the meantime, you can follow some simple rules, namely not to use the same password for different sites, to ensure the complexity of these passwords, not to install pirate copies of games or software that may include a trojan and to regularly scan your system.
A humorous note to finish, from the CommitStrip webcomic, which illustrates the most used password from 2013 to 2017 namely “123456”.

ANY QUESTION ?





